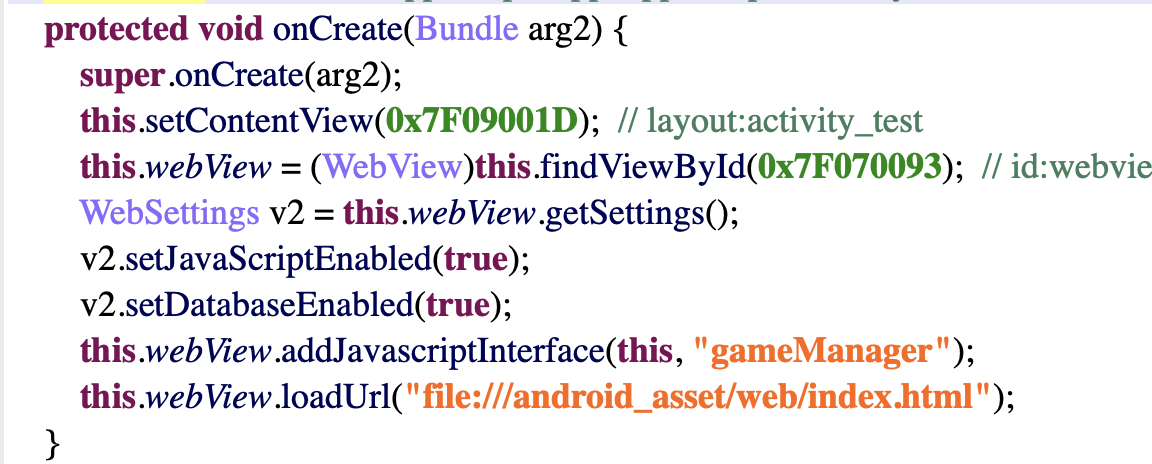
Load webview, a 2048 game. Click ten times in MainActivity to enter TestActivity, but it is invalid after clicking. It is guessed that the button may be hidden. I don’t know where it is, and I don’t need to analyze the layout file. I can directly use the command adb shell am start -n com.test.hufu22/.TestActivityto enter the game interface. There is a JS interface in TestActivity,
When we look under assets, we will find that game_manager.js is confused, there should be key logic, and then analyze the Native file.
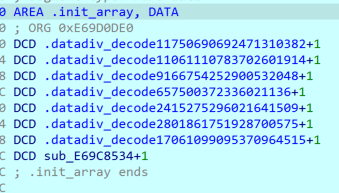
init_array has a large number of strings decrypted, almost all useful strings are encrypted.
Then a function is called. There are multiple similar functions in the so file, which are anti-debugging and anti-Frida hooks, and directly Nop all these calls. After entering JNI_OnLoad, a check function is dynamically registered, and it can be seen that it is a check only after the string of init_array is decrypted.
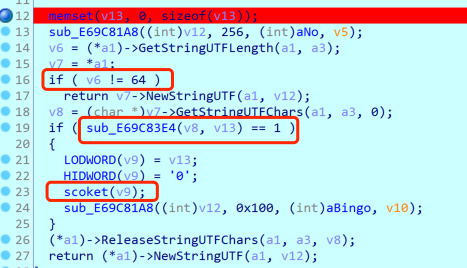
Analysis check function:
The length of the parameter passed in first is 64, and then sub_E69C83E4 is called, follow-up analysis:
The string of length 64 becomes 48 through a function, and the first guess is base64, although the encoding table in it is very strange. Get the result of base64 decryption, and then perform AES encryption (the S box was modified, but I didn’t pay attention at the time), the key is byte_E69D1310 here, which will be dynamically modified, which will be mentioned later. After completing these tasks, use the result of AES encryption as the parameter of the socket function (I modified the function name to socket), and follow up the analysis:
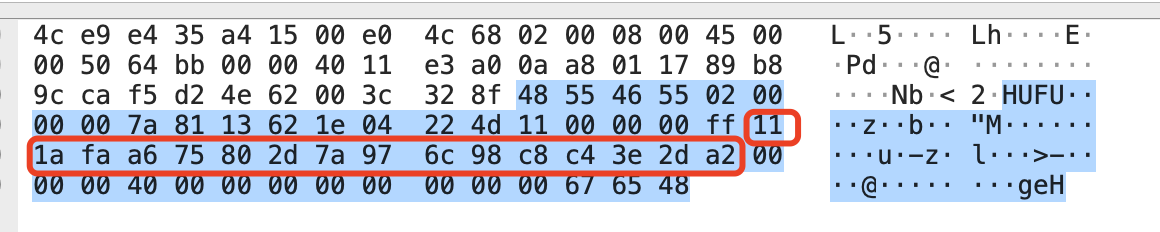
There are some functions in it, which will define a data format, and then use sendto to send, that is, the given traffic file. There are roughly two formats:
1 | |
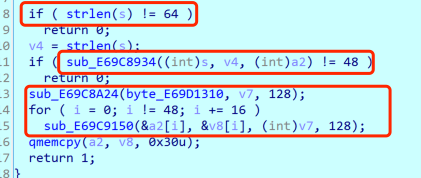
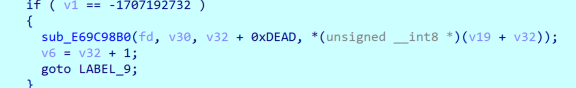
Follow up the above function for analysis:
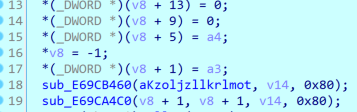
It can be known that strings2 is the result of encrypting the third and fourth parameters, the third parameter is i+0xdead, the fourth parameter is *(i+v19), and v19 is the parameter passed in by the socket. Extract the data in the packet and decrypt the following parts:
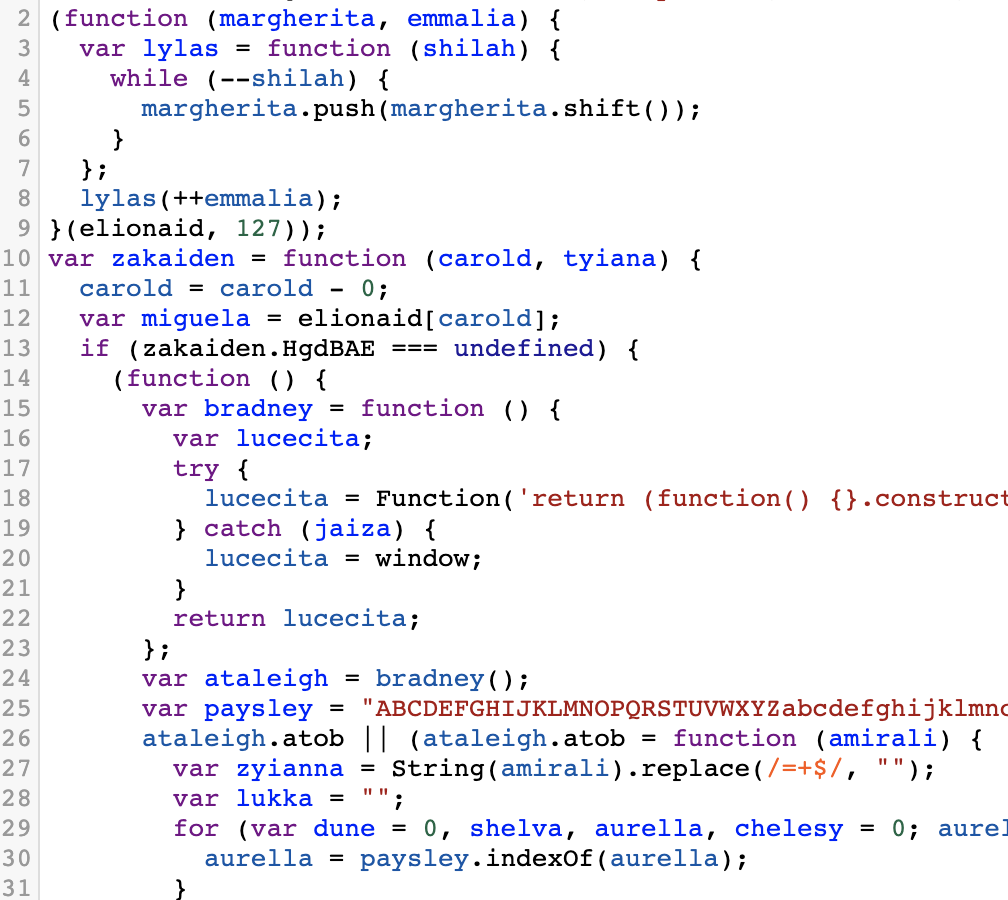
We have almost analyzed the so file. Next, we will analyze the JS code and see that the obfuscation will die directly. Using this website can remove some obfuscation ( javascript deobfuscator), but there are a lot of base64 strings in it. Analysis The first two functions:
The guessing function should be to reverse the order of the base64 string array at the beginning, and then decrypt the base64. There will be a large number of array indexes in the code, and we will restore these names (the name is not fixed after each de-obfuscation using the website):
Write code to restore the function name. Use the following script to restore most functions. The writing is not perfect ( xxxx) + "xx"this kind of string will appear), and regular matching can be used to improve:
1 | |
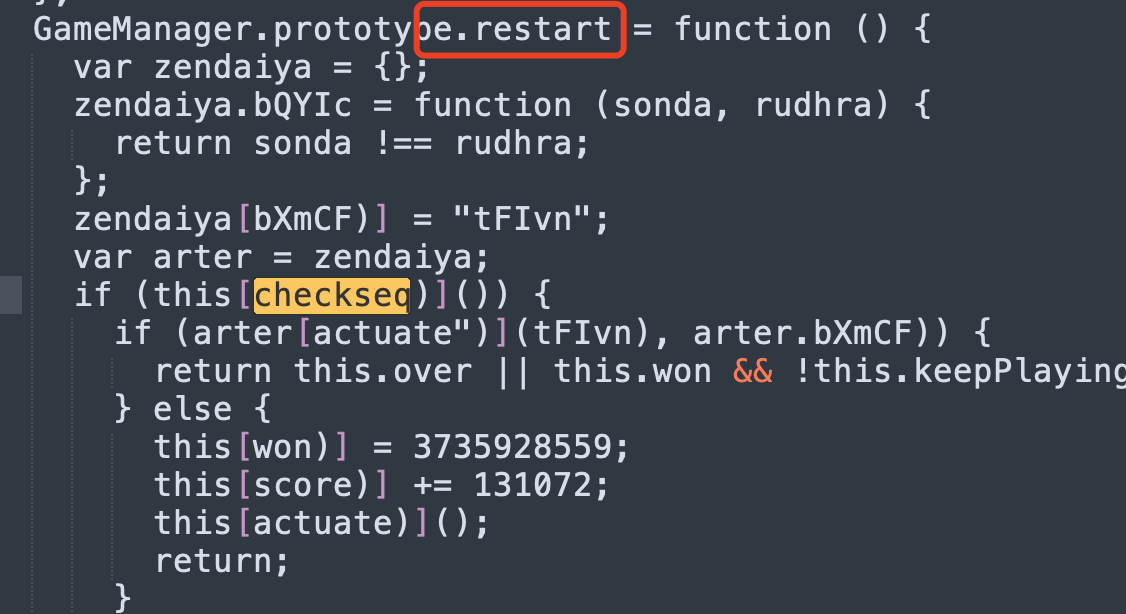
After decryption, go to docheck first, and call dockeck in the function GameManager.prototype.checkseq:
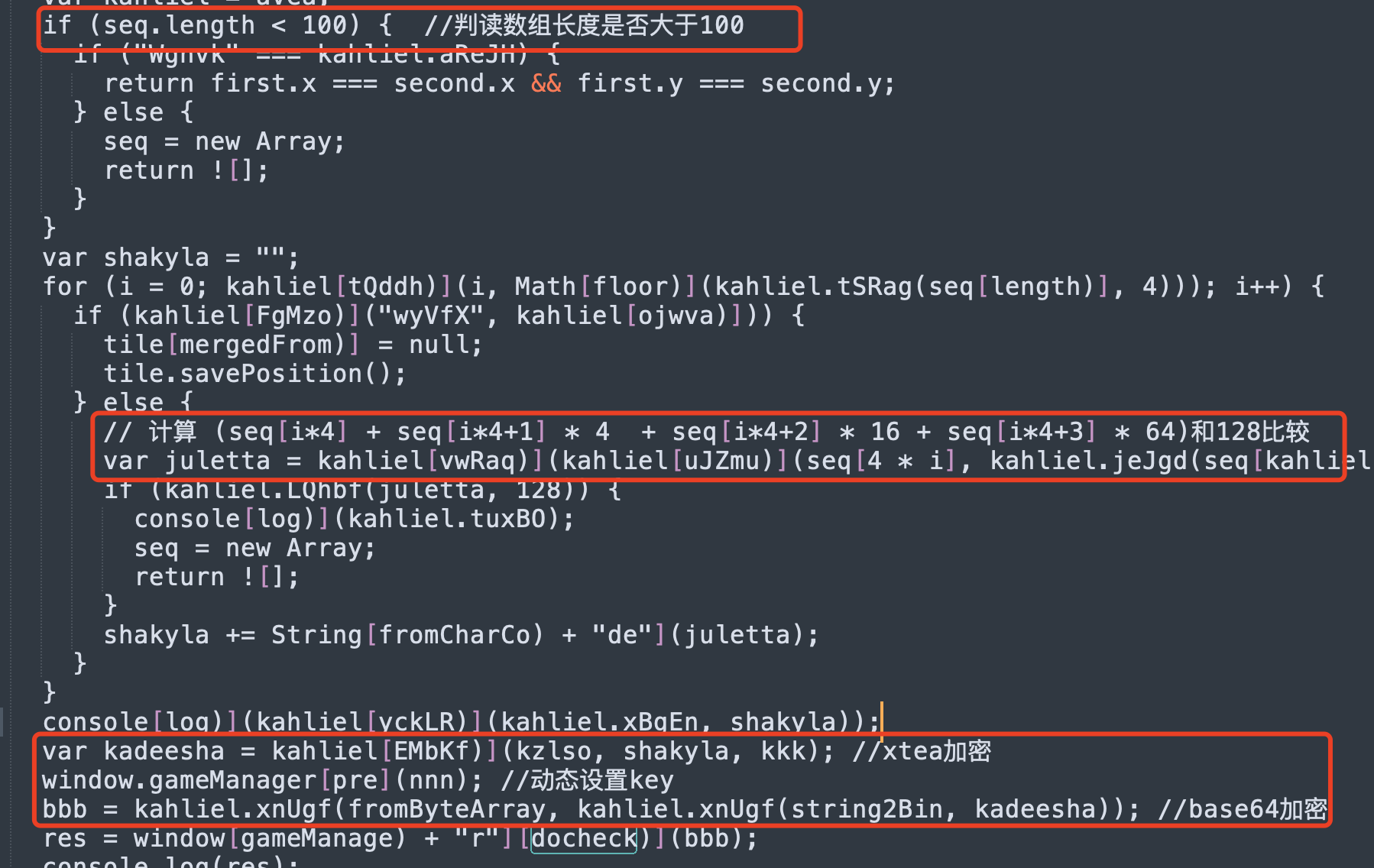
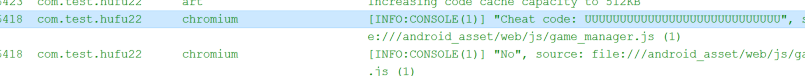
There are no cross-references, everything is located based on the search string. . . The general logical analysis is clear. Only when the length of seq is greater than 100 and within the range of 128 after a calculation can docheck be called, and the cheat code will be printed. Let's see where checkseq is called.
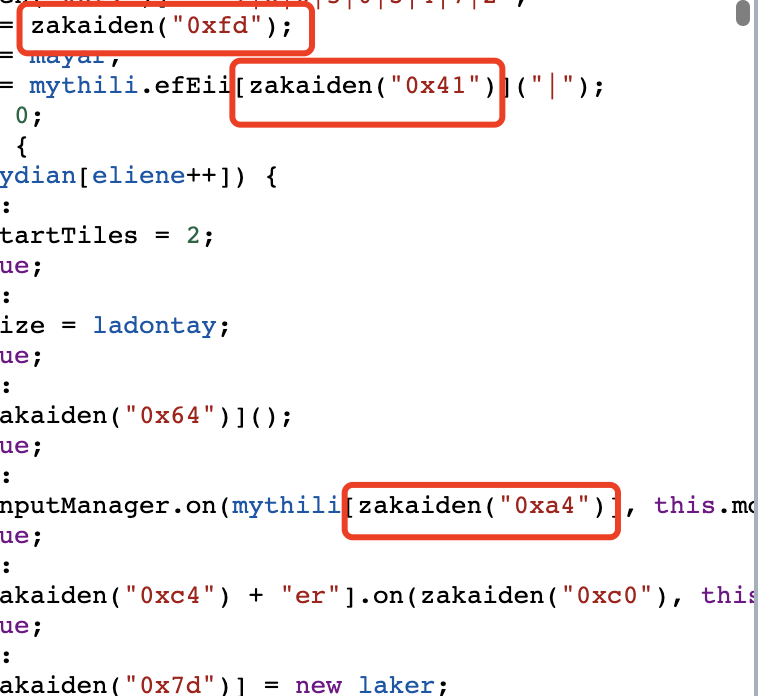
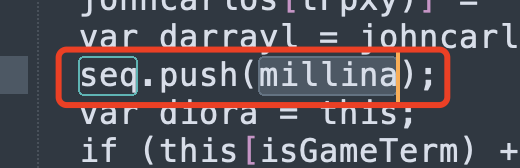
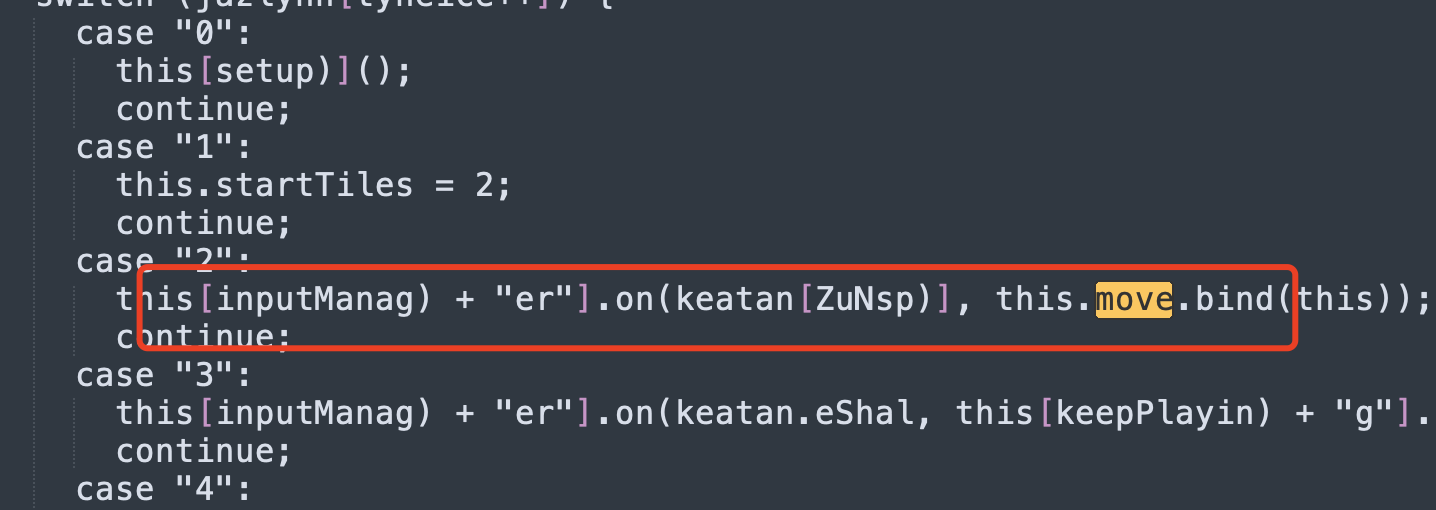
Then search for seq to see how seq adds data. It is found in GameManager.prototype[move)] that move may be a sliding box:
While tracking move:
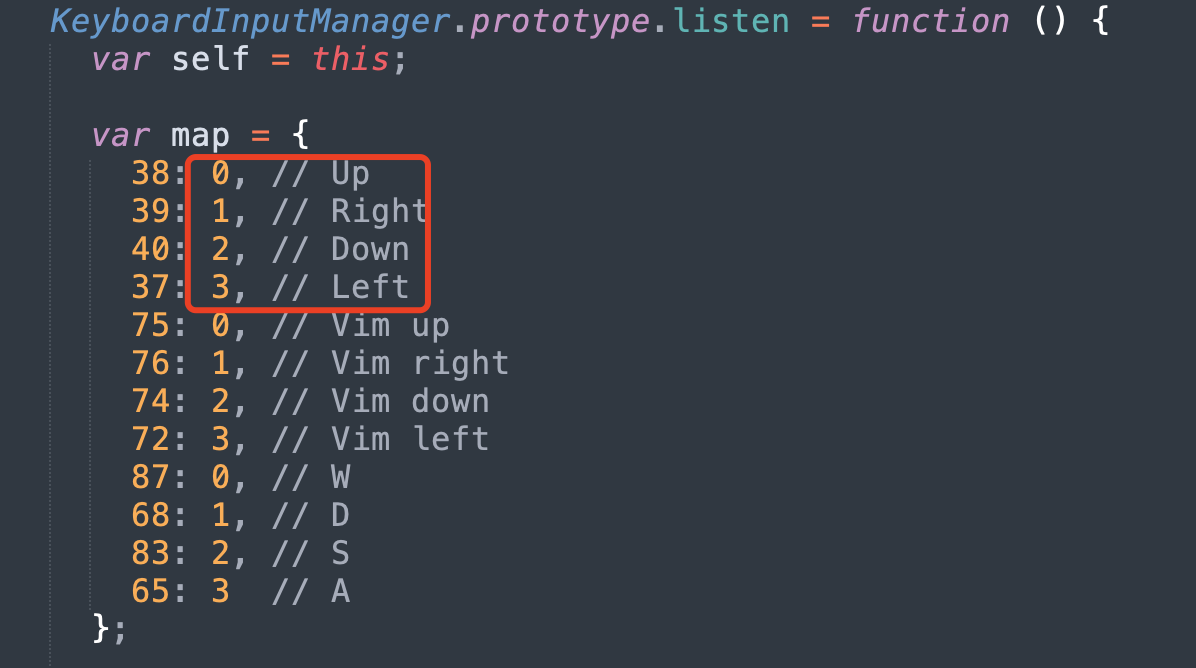
Here we see inputmanager, which we can find in other js files:
So seq records the direction of sliding. I thought about it, must it be the movement of the slider to count? Then I swipe right 100 times, click on newgame, and successfully output the cheat code.
1 | |
1 | |
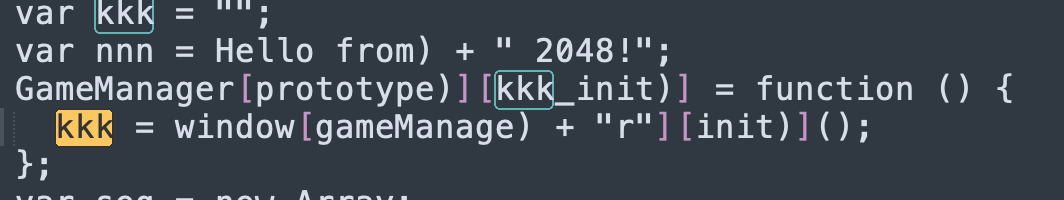
Then use the modified AES decryption of the S box, the decryption code is too long to paste, paste a calculation inverse S box, the key is Hello from 2048!
1 | |
Then perform Xtea decryption, the key is (up, up, down, d:
1 | |
Decrypt to get the flag.
fpbe
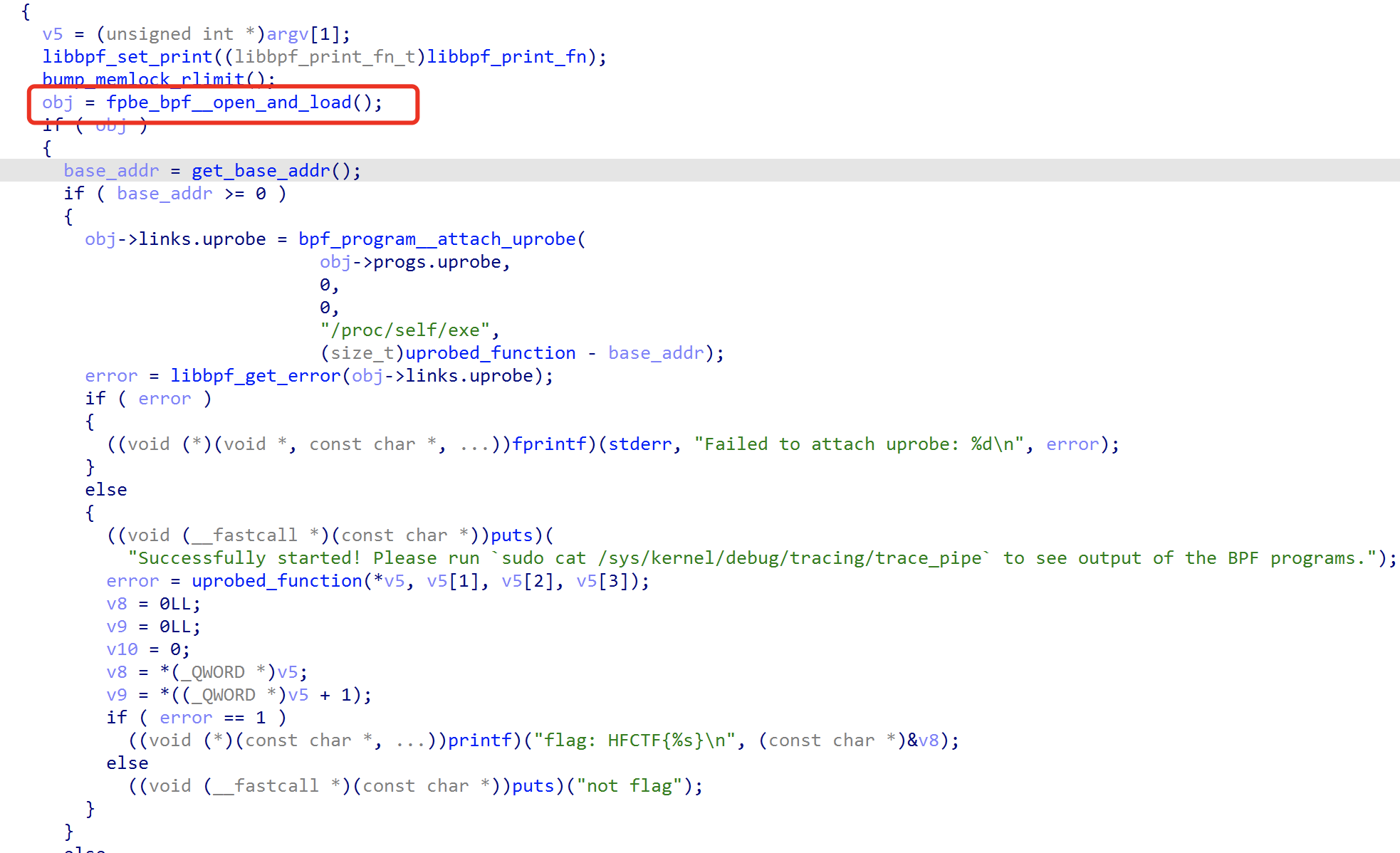
After getting the title and analyzing it for a long time, I found that it is necessary to blast sha256, but it is obviously impossible, and then search for what this bpf is, and finally determine the key points.
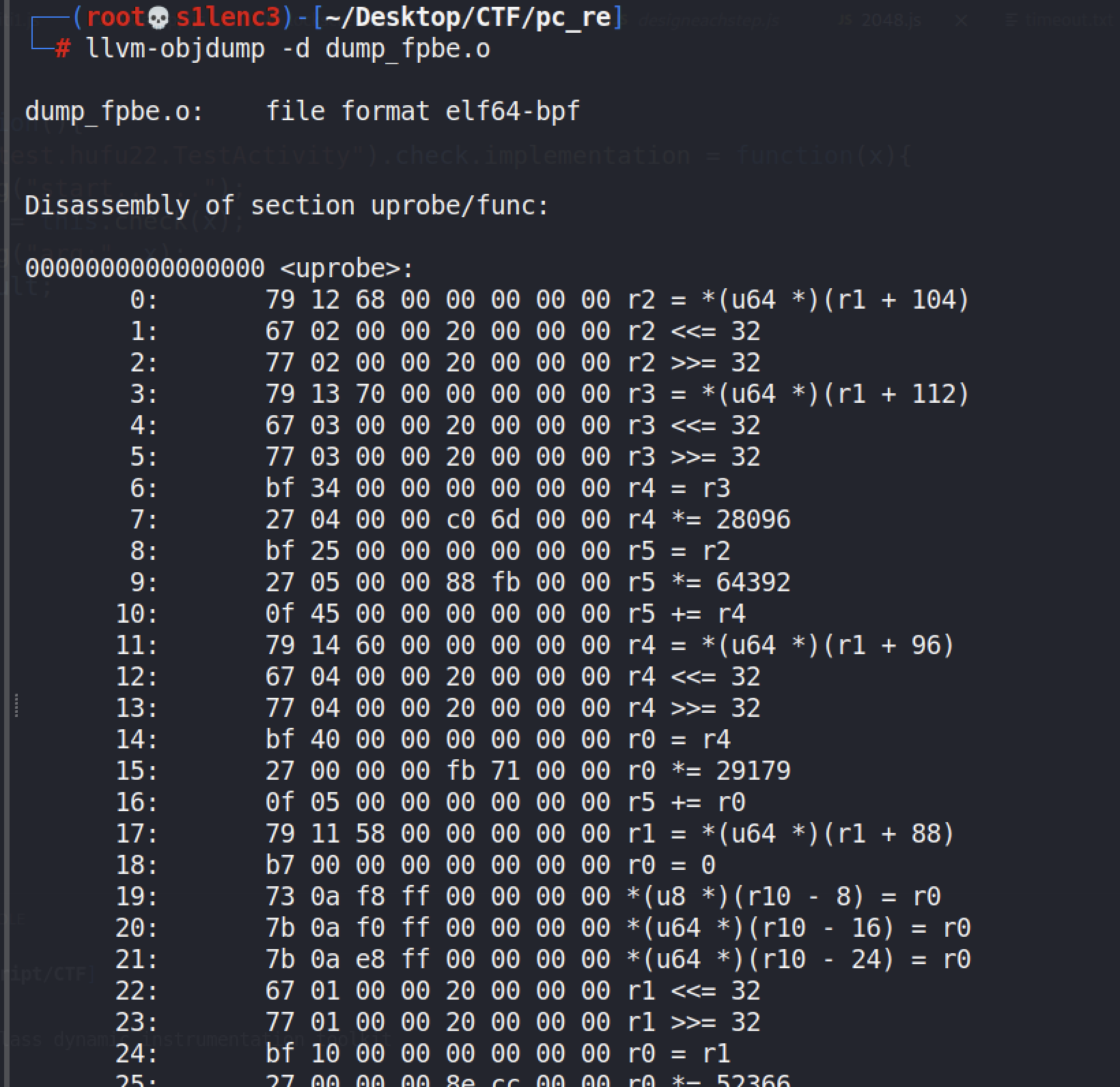
A bpf-like ELF file will be loaded in it, and when the dump comes out, it is found that IDA does not parse it, and then searches for disassembly, llvm-objdump will do.
The logic is directly given, just decrypt it, and solve it with z3 constraints.
1 | |
the_shellcode
themida, will not shed its shell, a waste one. . .
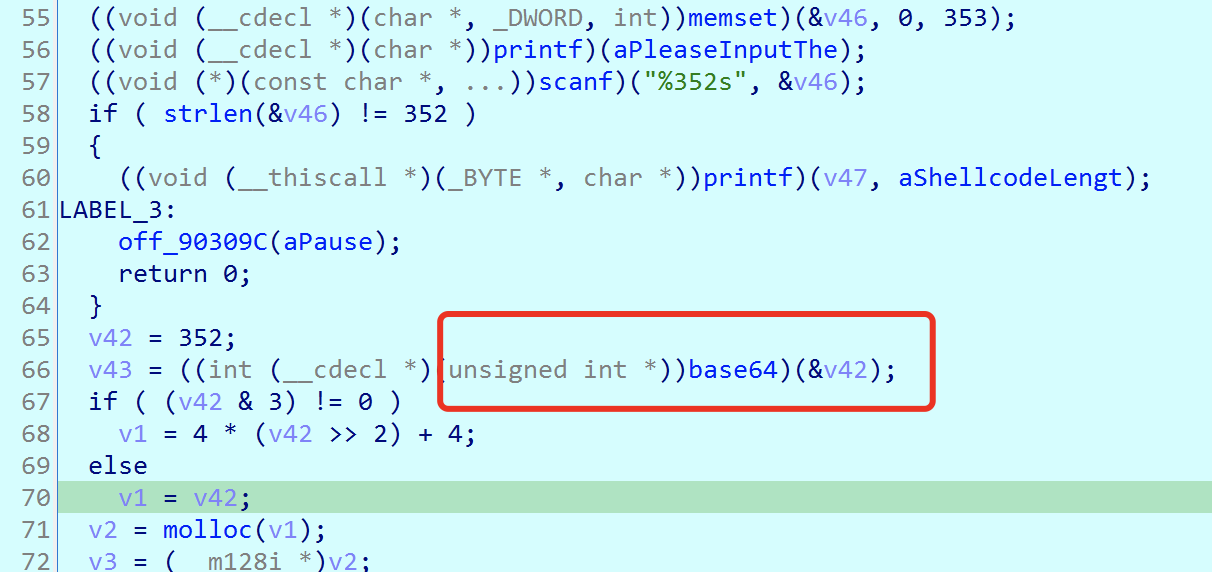
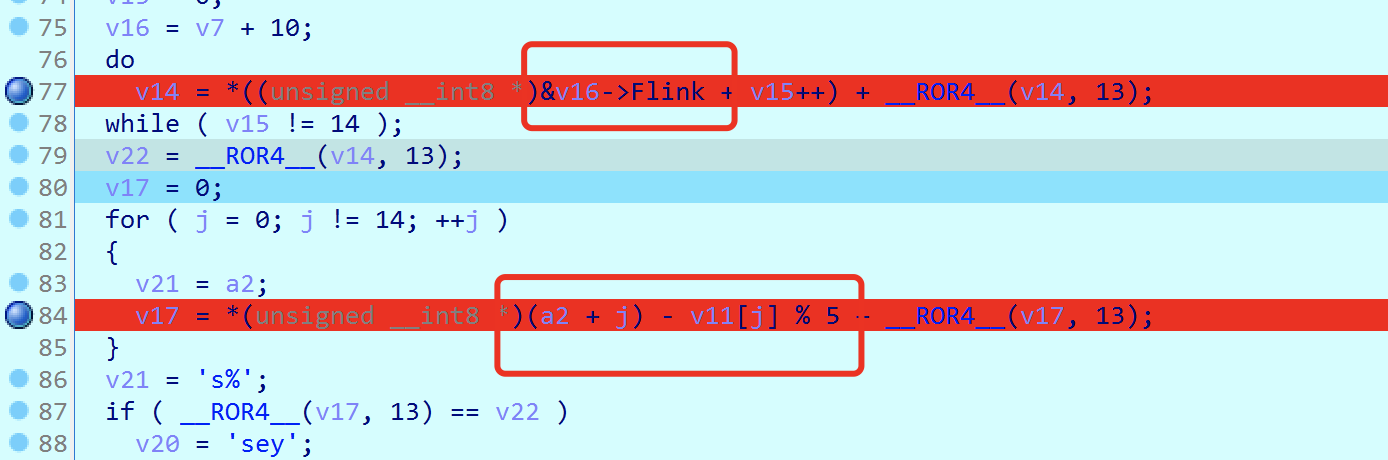
Start two processes, attach these two processes, OD is used to locate the key code part, and view the pseudocode in ida combined with the address located by OD.
First perform base64 decryption:
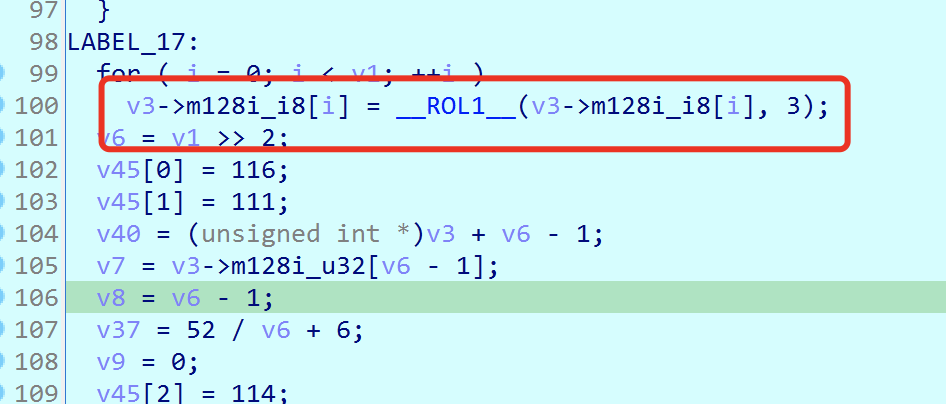
Then each character is rotated to the left by 3 bits,
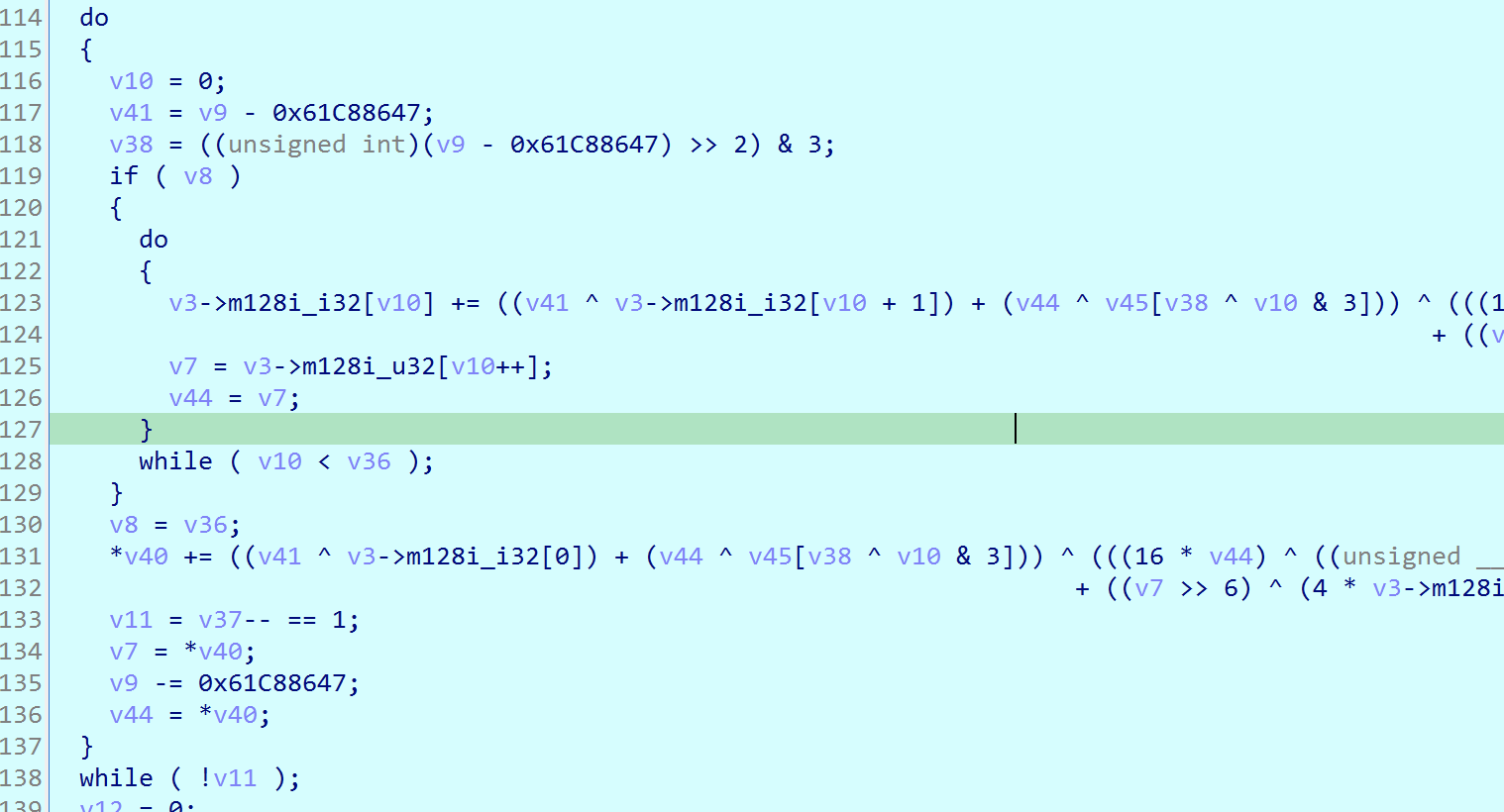
xxtea magic modification encryption:
Knowing the encryption process, we solve the shellcode:
1 | |
Then load the shellcode:
1 | |
Breakpoint debugging:
In fact, it is to compare these two, get the data directly through debugging, and decrypt:
1 | |
Finally, you can find md5 according to the prompt:
1 | |
Comments
Post a Comment